AnnouncementCocoon Data have launched Qanapi - an encryption platform of the future.
Learn moreITAR Cloud Compliance

Cloud solutions for compliance and regulated data take a monumental burden off of businesses. Compliance directives such as ITAR and EAR apply to your business regardless of your resources or ability to become compliant. Maintaining compliance and reducing the IT burden on your business are no longer mutually exclusive. Trust a proven, ITAR compliant, security solution and access your data with ease using Cocoon Data for ITAR.
Cocoon Data Cloud Compliance Toolkit
- Document Sharing
- Collaboration
- Insider Threat Defense
Document Sharing
No document management solution is complete without the ability to share. Cocoon Data provides easy and secure file sharing. Users and administrators have a plethora of security features that can be layered on to make sure data goes where it’s needed and nowhere else.
- Rule based access controls
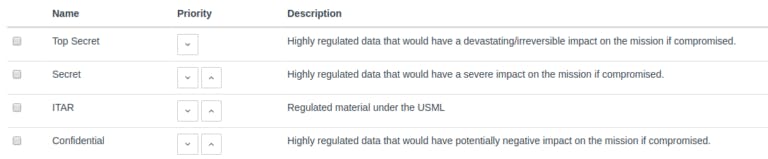
- Click and Share
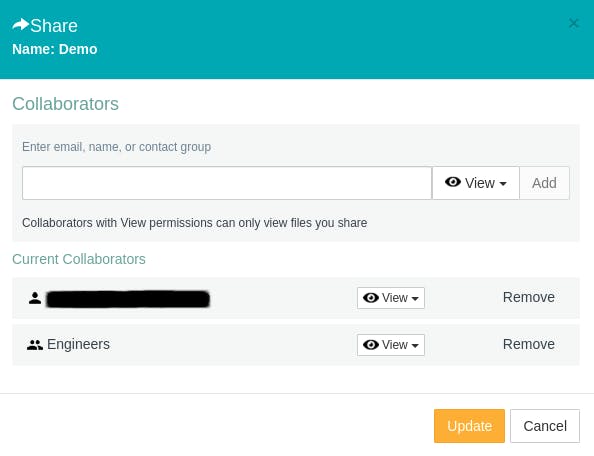
- Time-based rules of expiration of shared files

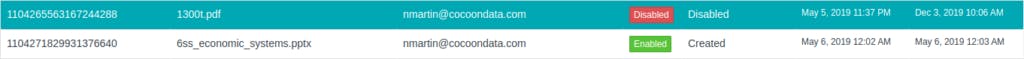
- Disable file access with one click
Collaboration
Fast and easy collaboration is a necessity that doesn’t magically go away once the data is classified. Give your personnel a strong collaborative solution that is ITAR and EAR compliant. We know the frustration of having to deal with legacy systems that claim to provide compliant cloud solutions, but still relies on downloading regulated material to the host machine.
Cocoon Data for ITAR uses a modified and highly secure version of O365 that we manage and host in FedRAMP validated environments. Our cloud compliance toolkit includes this compliant version of O356 for in cloud collaboration of regulated data. Our collaborative toolkit doesn’t require you to download your documents to edit them. Truly compliant cloud collaboration for regulated data is available now.
Insider Threat Defense
One of the greatest threats in cyber security is the insider threat. While most acknowledge this threat there seems to be a resignation to it. An “oh well” attitude is a dangerous line of thought in our field. We refuse to allow this way of thinking to affect our security principles.
Enter our Insider Threat Defense systems. Cocoon Data for ITAR by default assigns full control of data to the data owner. No permissions are given to anyone else, even the administrators, without deliberate action by the data owner. Want to learn more about why administrator data visibility is a bad idea?
Read more on ITAR Compliance here.