AnnouncementCocoon Data have launched Qanapi - an encryption platform of the future.
Learn moreThe Hon. Christopher Pyne Hosts Cybersecurity Event

Following several large-scale cyber attacks on Australian Governments and Businesses, Cocoon Data hosted an event with the former Defence Minister, the Hon Christopher Pyne, and Cocoon Data’s Chairman and CEO, Trent Telford.
Over 40 people attended this cybersecurity event, including senior public servants and advisors from a range of government departments to learn about a range of technologies that can assist in mitigating risk and improving operational capability.
The Hon Christopher Pyne and Trent Telford took this opportunity to identify the main problems government departments are facing in this new working from home environment, before outlining the data-centric military grade security solutions Cocoon Data has created after years of experience as a global technology company.

Cybersecurity and secure file sharing in the work from home environment
Over the past two years, Australia has been the target of several large-scale cyber malicious attacks that have spanned all levels of government, businesses, political organisations, education and health.
Prime Minister Scott Morrison announced in his courtyard press briefing after the most recent attack in June 2020: “Based on advice provided to the Government by our cyber experts, the Australian Cyber Security Centre (ACSC), Australian organisations are currently being targeted by a sophisticated state-based cyber actor.
“This activity is targeting Australian organisations across a range of sectors, including all levels of government.”
The threat is real and we are all feeling the effects. And in addition, COVID-19 brings with it the additional challenges of working from home and trying to secure and share sensitive data in the cloud.
So how can government agencies protect the sensitive data they hold?
Enforcing agency access policy against personnel clearances and file classifications in the cloud
The main problem with Government networks, as outlined by Telford, is, “they are physical and were designed to plug into or dial into, from the outside in”.
“They weren’t designed for mobile devices and cloud, let alone the huge upheaval of work from home that COVID-19 brought on. These networks were designed as inward facing protective walls with internal logic to segregate data based on classification. They weren’t designed to have that classification and policy framework in the cloud.
“And now, I think most would agree, WFH flexibility is here to stay, in some form, for the long term. The paradigm has shifted and shifted fast.”
“Governments still need to do their job with sensitive data and calling into VPN’s provides a bandaid for now. But how do we look to the future?
“Cocoon looked at this problem years ago and went a long way to solving it with the ability to enforce agency access policy against personnel clearances and file classifications in the cloud AND with unprecedented levels of control and underlying security.
“We do this by making sure each file has its own unique encryption key and we can apply all sorts of rules, such as no printing, no downloading, no copying and pasting, etc. We can even set a “Time Bomb” where access only lasts for this time and date, for a matter of hours or days, before the ‘key is killed’ and your data effectively “crumbles”.
Classified file geofencing in secure cloud environments
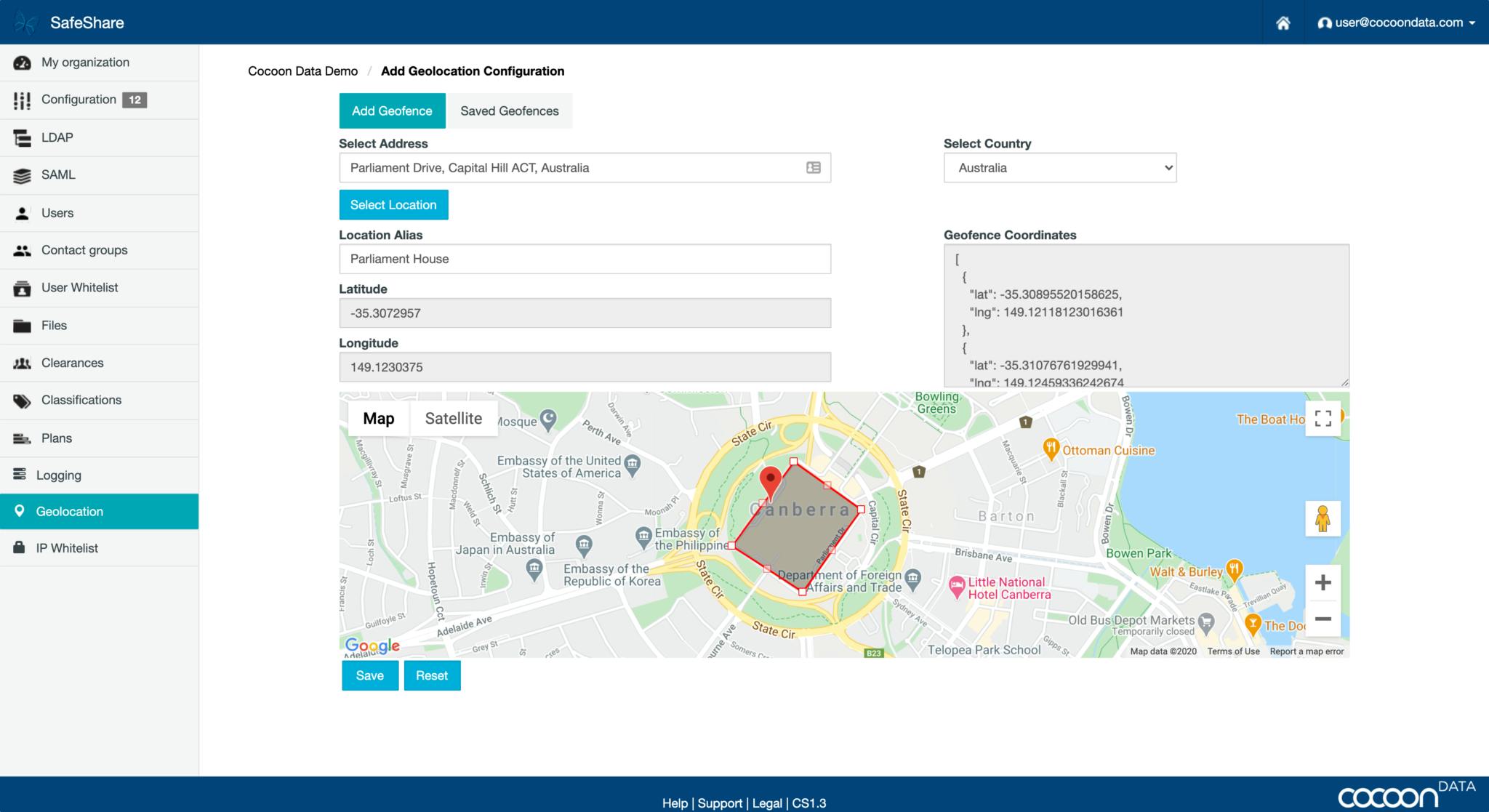
Telford also explained another way Cocoon can help secure government data by using an innovative feature of Cocoon Data called geofencing.
“Classified file geofencing in secure cloud environments means we can control flexible ‘on/off’ rules to a single file (or groups) depending on where the person is standing – anywhere in the world.
“For example, let’s say you have 1,000 files – 700 of which are unclassified and 300 classified
– and your iPad has access to this content within your office in Parliament House. While you are moving through the building geofencing allows you to access all this classified and non-classified content on your iPad.
“But once you leave the building and go to access a classified file named PMPV10-4 this message pops up – ‘sorry you are not authorised to access this file as you are outside the authorised perimeter’. But when you click on another classified file, PMRES10-4 you can open it. That’s because it was deemed safe to be opened on this device but only while on Australian sovereign soil.
“200 of your 300 classified files sit within the ‘Australia’ geofence, 100 sit within the Parliament house geofence. The 700 unclassified are not geofenced. All are properly governed with unique encryption keys for each file and tied to your clearance and your location.
“This means you can’t accidentally view or share information outside of where it is deemed safe.”
Protection from major security breaches
Another example shared by Telford on the night shows how geofencing can also protect government staff from major security breaches while travelling overseas.
“Let’s say you’re a valued member of DFAT, posted in Abu Dhabi. Cocoon Data is connected to the Security Operations Centre of your department where they run big room sized screens where security incidents are tracked.
“You leave the embassy Friday afternoon for a weekend relaxing and thanks to good governance, only 20 of the 500 of your files in the DFAT Cocoon Data cloud can be accessed outside the walls of the embassy and those 20 only within Abu Dhabi – for your own protection.
“Unfortunately, en-route to Oman beachclub you are targeted and driven across the border but into Saudi Arabia. You are forced to attempt to open files located in your Cocoon Data cloud drive.
“Not only are no keys released with a message saying so, but the DFAT SOC is alerted to a major security breach on the big screen. In addition, your Lat/Long location was immediately flashed up on the big screen and diplomacy kicks into action. In another scenario a ‘silent alarm’ file was opened where the keys were released to a ‘classified file’ but the same SOC event was triggered – thus your adversary was none the wiser…
“No other software company in the world can do this level of security tied to SIEM/SOC integration for single file access.”
Conclusion
According to Telford, the cybersecurity event on the Challenges of Work from Home for Government provided public servants and government advisors with new and meaningful insights on the protection of data in a post-COVID working environment.
“We were thrilled to have Christopher Pyne host this panel for us, sharing insights from his many years of experience in the Federal Government, dealing with cybersecurity issues both here and overseas.
“This evening was a great success with engagement and one-on-one serious interest from a lot of government agencies. We have already formed new partnerships with genuine interest from a lot of federal agencies.
“As I said on the night, we have the experience here, and in the US and in the UK that can help to inform your world and augment Australian guidelines. We are Australian and we won’t overreach – we want to help you solve the problem by being part of the solution.”
If you’re looking to work with an Australian technology company who delivers data-centric military grade security solutions for government and business data,talk to us.
Find out more.
Published
Aug 25, 2020