Considering CMMC 2.0 Self-Attestation? Here’s What You Should Know First

We’ll get right to the point: you may have heard recently that with CMMC 2.0, you can self-attest your organization’s compliance. This is true, but there’s more to it than that.
Under CMMC 1.0 , all organizations would have had to be audited by a third party (CP3AO). With CMMC 2.0, self-attestation is possible, but only for organizations not required to undergo a C3POA audit by the DoD. Also, there are pros and cons to self-attesting. We’ll get into that later in this article. First, let’s walk through the CMMC 2.0 requirements, so you’ll have an idea of whether or not self-attesting will be available to your organization.
CMMC 2.0 in a Nutshell
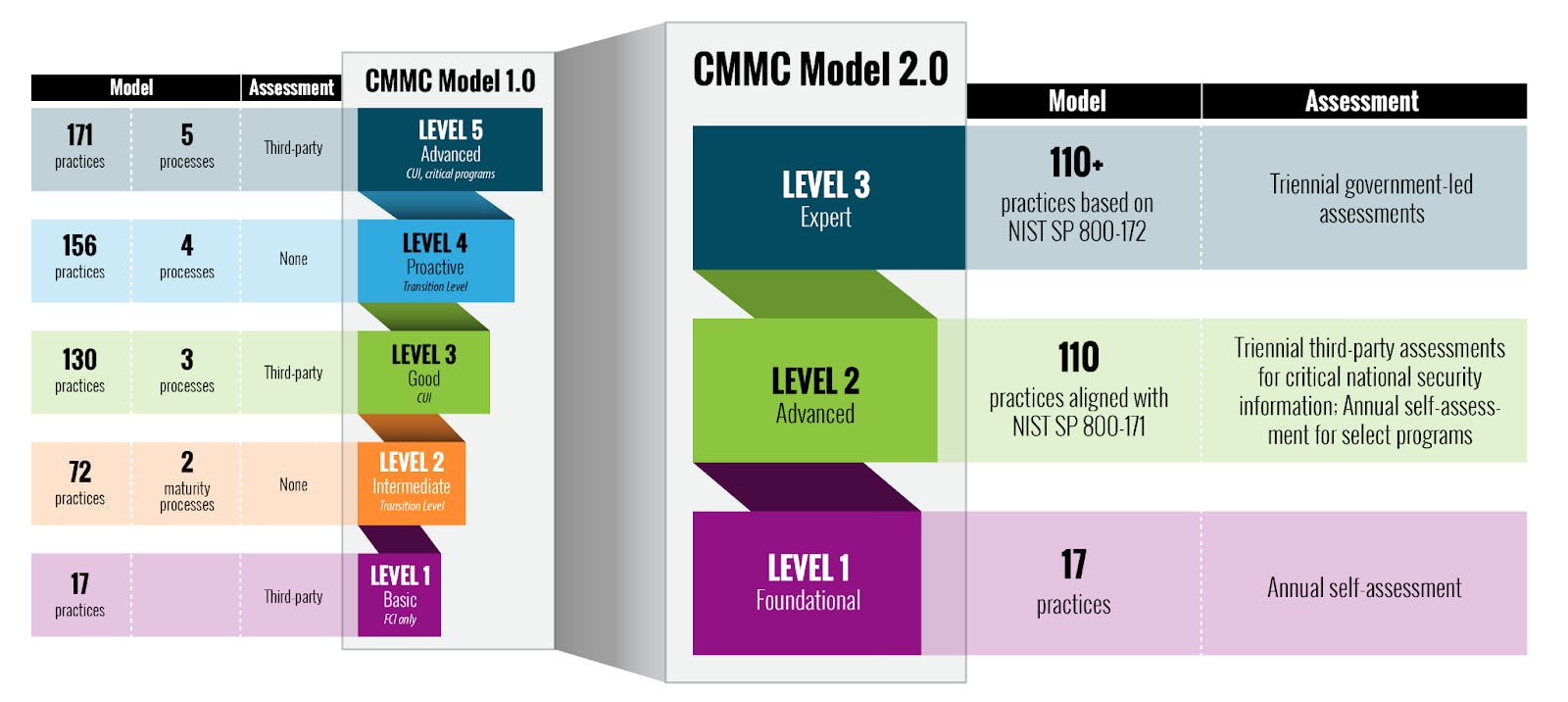
The CMMC 2.0 Level 1 requirements revolve around federal contract information (FCI). If your organization works under a federal contract and handles FCI, that information is protected by 17 sets of security practices. These practices are based on the NIST 800-171 framework.
Today, many companies suddenly find themselves with the option to self-attest under CMMC 2.0. With this option, C-level executives must attest that their organizations are adhering to the security practices. This option is also only available to companies that are considered to be at CMMC 2.0 maturity level 1 and non-prioritized companies at level 2.
CMMC level 2 is bifurcated where some companies are allowed to self-attest and others are not depending on the sensitivity of their information. A good example would be a company that provides boots for a military base. Sure, every soldier needs to wear boots, but the information regarding this piece of equipment may not be considered critical national security information by the DoD.
When such a company self-attests, they must first write a System Security Plan and a Plan of Action and Milestones (POA&M). The POA&M will generally include any compliance areas the company hasn’t covered but plans to. Once the contract is signed with the government, the company typically has 180 days to remediate each area of weakness it has included in the POA&M. But certain serious weaknesses can prevent a company from landing federal contracts.
Companies must submit their compliance findings to the Supplier Performance Risk System (SPRS), the DoD’s designated application for receiving suppliers’ performance information. They will receive a compliance score that ranges from -300 to 110, which they must report to the DoD. Companies will need to update their CMMC 2.0 self-attestation on an annual basis.
When an organization is found to be out of compliance, the DoD can take remedial actions—which may include civil penalties if the DoD believes the company deliberately made false claims. It’s interesting to note that the DoD hasn’t announced a minimum score requirement for certain types of contracts, but we’re expecting to hear that information soon.
That’s just the first part of maturity level 2. Companies that are working in high-priority areas—such as building tanks or missiles—are held to an even higher standard and fall under either level 2 or level 3, where self-attestation is not possible. These companies generally handle controlled unclassified information (CUI), which, by law, must be protected. Every three years, they must undergo a CMMC C3PAO audit by a third party.
Pros and Cons of CMMC 2.0 Self-Attestation
You may not know right now if you will be required to undergo a C3PAO since your compliance requirements will be defined in the contractual agreement with the DoD. If you are required for an external audit then you won’t have the option to self-attest. Let’s assume you can self-attest. What are the pros and cons of doing so?
The main advantage to self-attestation is that you will save money by carrying out the audit with internal resources.
However, if you plan on doing a CMMC 2.0 self-attestation, you still must implement the appropriate controls over your systems and data. You’ll need rigorous access controls and must audit every system that will contain FCI or CUI.
Conducting the audit on your own will save you money, but it may end up taking more of your time. It may also put you at risk if you don’t have the right resources in-house to conduct it appropriately. Lastly, the CEO must sign off on the assessment that the audit was conducted correctly and that the results were true, which may highlight the risks with self-attestation.
Another element that makes a CMMC 2.0 self-attestation seem less appealing is the timeline. CMMC 2.0 was originally slated to be implemented at the end of 2025. Now, the DoD has stated that companies will be contractually obligated to adhere to CMMC 2.0 at the end of the rulemaking period, which is slated to last 9 to 24 months. Companies that choose to self-attest for CMMC 2.0 may or may not save themselves some time against this impending deadline. If they try to meet all the requirements by buying security systems piecemeal, they’re facing a tedious, time-consuming process. But if they buy a turnkey solution, they will be in much better shape.
No matter what you choose, one way to reduce the scope of what must be audited is to create a secure enclave for the storage and transmission of FCI and CUI. Many Cocoon Data customers are doing just that with the help of our file sharing solution. Not only does Cocoon Data provide an affordable way to implement 45% of the required 110 NIST 800-171 controls, but it can also reduce the scope of your audit. When auditors come in and ask to review your FCI or CUI security controls, you’ll be able to point them to a secure enclave.
Whether you can CMMC 2.0 self-attest or must use a third-party auditor, Cocoon Data has strategies and solutions that can reduce the time and expense of CMMC 2.0 compliance. To speak with a CMMC expert, click here >